Cybersecurity Services
Audit > Arm > Anticipate > Act
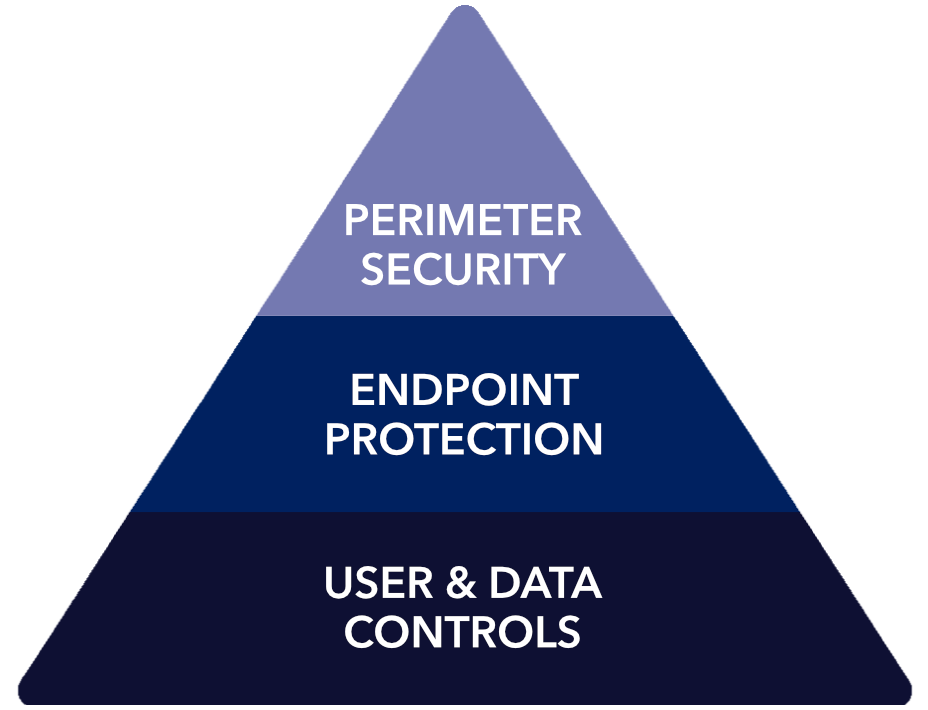
Defend your business with layered protection built for modern threats.
We reduce risk, harden your defenses, and support fast recovery—ensuring continuity and control in the face of cyber disruption.
Solutions
Explore below to see how our cybersecurity team translates layered security into real protection for your business.
-

Endpoint Threat Protection & Response
Stop threats before they spread.
Detect and neutralize malware, providing ransomware protection against advanced threats at the endpoint using behavioral analytics, real‑time threat isolation, and automated rollback. Monitored 24/7 by our partner’s U.S.‑based security operations center to keep every device—on‑prem or remote—secure and recoverable.
-

Email Security and Phishing Defense
Your inbox is the front line. We make it bulletproof.
We stop phishing, impersonation attempts, and email-based malware before it reaches your users. With AI-driven scanning, domain spoofing prevention, and advanced link and attachment protection, we also provide secure, encrypted email delivery when sensitive information needs to be sent or requested—allowing recipients to reply and upload files through a protected portal without exposing data to the inbox. All of this is delivered as part of our managed security services.
-

Identity and Access Management (IAM)
Identity is the new perimeter. We make it impenetrable.
From single sign-on (SSO) and multi-factor authentication (MFA) to just-in-time access and privilege reviews, we help ensure users only access what they need—when they need it.
-

Privileged Access Management (PAM)
No one should be a local admin—except when they should.
We control, monitor, and log all elevation requests, ensuring privileged actions are reviewed and revoked automatically.
-

Secure Backups
Your last line of defense, done right.
We deploy encrypted, tamper-resistant, and versioned backup systems that are regularly tested and off-site. Whether ransomware or accidental deletion, your data stays recoverable.
-

Attack Surface Management
Know your vulnerabilities before attackers do.
Continuous discovery, inventory, and monitoring of your external and internal assets to identify vulnerabilities, misconfigurations, and exposure points before attackers can exploit them. We align findings to frameworks like NIST and CIS for prioritized remediation and ongoing risk reduction with cybersecurity consulting to help your team implement fixes.
-

DNS & Web Threat Filtering
Protection that starts at the source—your internet traffic.
AI‑driven DNS filtering with real‑time threat intelligence and a cloud‑delivered web gateway to block malicious domains, phishing, malware, C2 callbacks, and data‑exfiltration before they reach any device. Includes HTTPS decryption, remote browser isolation, and a lightweight browser extension for granular control.
-

Cloud Security (Microsoft 365 and Google Workspace)
Collaborate freely—without compromising security.
Whether you're in Microsoft 365 or Google Workspace, we help you lock down user access, prevent data leakage, and detect threats across cloud apps, email, and file sharing platforms.
-

Security Awareness Training
Your users are your first line of defense. We train them like it.
From phishing simulations to gamified training modules, we deliver practical, high-impact education that helps staff recognize and stop threats.
-

Secure Data Disposal
Retire sensitive data the right way.
We offer NIST-compliant wiping and physical destruction for drives, devices, and paper records. Ensure sensitive data is unrecoverable before disposal or reuse.
Understanding Today’s Cyber Risks
Cyber criminals target small & midsize businesses with a wide range of attack methods.
According to Huntress’s 2025 Cyber Threat Report, the majority of cyber incidents in 2024 stemmed from infostealers (24%), malicious scripts (22%), and malware (17%), together making up over 60% of reported threats.
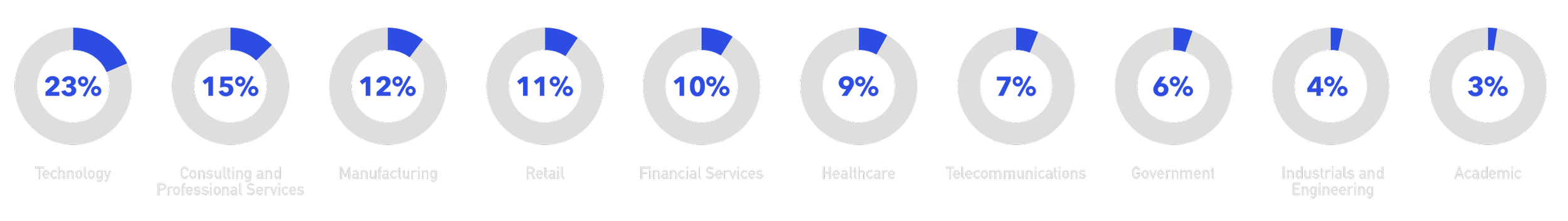
CrowdStrike’s reporting showed technology (23%), consulting (15%), and manufacturing (12%) as the most targeted industries, accounting for more than half of observed attacks across industry sectors.
Understanding these top sources of cyber threats highlights why a layered defense strategy is critical—and why CTRL-A prioritizes protection across every attack vector.
Top Cyber Threats in 2024 (%)
Source: Huntress Labs, "2025 Cyber Threat Report"
Top 10 Industries Targeted by Threat Actors in 2024
Source: CrowdStrike, Inc., “2025 Global Threat Report”

Recognize the Risk. Regain Control.
If your industry is showing up in these threat reports, it means attackers are actively probing businesses like yours. But risk doesn’t have to turn into reality.
Our portfolio of cybersecurity solutions leverages proven, best-in-class platforms to help you reduce risk, maintain operational continuity, and meet evolving security requirements.

Security That Aligns With Your Industry
For many industries, defending against cyber threats is only part of the challenge—frameworks like HIPAA, CMMC, SOC 2, CCPA, and the FTC Safeguards Rule also set specific requirements for how covered organizations must protect sensitive data.
Whether your business is working toward meeting formal compliance standards or simply aiming to strengthen its defenses, we’ll help you get ahead—and stay there.
Let our defenders take it from here.
Related Services
Security planning is often paired with:
U.S.-Based Workforce
All IT management and support at CTRL-A is performed by employees and vetted contractors under binding agreements such as NDAs. No third parties, outsourcing firms, or foreign nationals are granted access to our systems or client environments. To meet compliance requirements, all staff are U.S. citizens based in the United States.

Platform Disclosure Policy
Our security stack is built on layered, best-in-class platforms tailored for resilience and scale. While we don't publish tool specifics online for security reasons, we’re happy to discuss our technology ecosystem under NDA or during formal engagement.